Cyber Tools
Nemesis is an offensive data enrichment pipeline and operator support system.
https://github.com/SpecterOps/Nemesis
https://github.com/SpecterOps/Nemesis
SessionProbe is a multi-threaded pentesting tool designed to assist in evaluating user privileges in web applications. It takes a user's session token and checks for a list of URLs if access is possible, highlighting potential authorization issues. SessionProbe deduplicates URL lists and provides real-time logging and progress tracking.
https://github.com/dub-flow/sessionprobe
https://github.com/dub-flow/sessionprobe
Mosint is an automated email osint tool written in Go that allows you investigate for target emails in a fast and efficient manner. It consolidates numerous services, enabling security researchers to swiftly access a wealth of information.
https://github.com/alpkeskin/mosint
https://github.com/alpkeskin/mosint
MasterParser stands as a robust Digital Forensics and Incident Response tool meticulously crafted for the analysis of Linux logs within the var/log directory. Specifically designed to expedite the investigative process for security incidents on Linux systems.
https://github.com/securityjoes/MasterParser
https://github.com/securityjoes/MasterParser
Adalanche gives instant results, showing you what permissions users and groups have in an Active Directory. It is useful for visualizing and exploring who can take over accounts, machines or the entire domain, and can be used to find and show misconfigurations.
https://github.com/lkarlslund/Adalanche
https://github.com/lkarlslund/Adalanche
Wazuh is a free and open source platform used for threat prevention, detection, and response. It is capable of protecting workloads across on-premises, virtualized, containerized, and cloud-based environments.
https://github.com/wazuh/wazuh
https://github.com/wazuh/wazuh
Vigil is a Python library and REST API for assessing Large Language Model prompts and responses against a set of scanners to detect prompt injections, jailbreaks, and other potential threats. This repository also provides the detection signatures and datasets needed to get started with self-hosting.
https://github.com/deadbits/vigil-llm
https://github.com/deadbits/vigil-llm
PolarDNS is a specialized authoritative DNS server that allows the operator to produce custom DNS responses suitable for DNS protocol testing purposes.
https://github.com/oryxlabs/PolarDNS
https://github.com/oryxlabs/PolarDNS
Kubescape is an open-source Kubernetes security platform, built for use in your day-to-day workflow, by fitting into your clusters, CI/CD pipelines and IDE. It serves as a one-stop-shop for Kuberenetes security and includes vulnerability and misconfiguration scanning.
https://github.com/kubescape/kubescape
https://github.com/kubescape/kubescape
Velociraptor is a sophisticated digital forensics and incident response tool designed to improve your insight into endpoint activities.
https://github.com/Velocidex/velociraptor
https://github.com/Velocidex/velociraptor
LLM Guard by Protect AI is a comprehensive tool designed to fortify the security of Large Language Models (LLMs). By offering sanitization, detection of harmful language, prevention of data leakage, and resistance against prompt injection attacks, LLM-Guard ensures that your interactions with LLMs remain safe and secure.
https://github.com/protectai/llm-guard
https://github.com/protectai/llm-guard
Yeti serves as a unified platform to consolidate observables, indicators of compromise, TTPs, and threat-related knowledge. It enhances observables automatically, such as domain resolution and IP geolocation, saving you the effort.
https://github.com/yeti-platform/yeti
https://github.com/yeti-platform/yeti
Navigate the Common Vulnerabilities and Exposures (CVE) jungle with ease using CVEMAP, a command-line interface (CLI) tool designed to provide a structured and easily navigable interface to various vulnerability databases.
https://github.com/projectdiscovery/cvemap
https://github.com/projectdiscovery/cvemap
EMBA is designed as the central firmware analysis tool for penetration testers and product security teams. It supports the complete security analysis process starting with firmware extraction, doing static analysis and dynamic analysis via emulation and finally generating a web report.
https://github.com/e-m-b-a/emba
https://github.com/e-m-b-a/emba
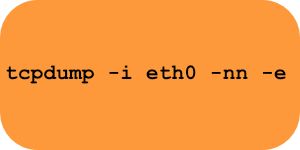
Commands to troubleshoot the different OSI layers
Here are a set of Linux commands you can learn to troubleshoot the various OSI layers.
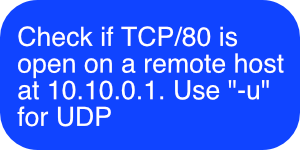
The primary focus of the transport layer is to ensure that data packets arrive in the right order, without losses or errors, or can be seamlessly recovered if required. Flow control, along with error control, is often a focus at the transport layer. At this layer, commonly used protocols include the Transmission Control Protocol (TCP), a near-lossless connection-based protocol, and the User Datagram Protocol (UDP), a lossy connectionless protocol. TCP is commonly used where all data must be intact (e.g. file share), whereas UDP is used when retaining all packets is less critical (e.g. video streaming).
The physical layer refers to the physical communication medium and the technologies to transmit data across that medium. At its core, data communication is the transfer of digital and electronic signals through various physical channels like fiber-optic cables, copper cabling, and air. The physical layer includes standards for technologies and metrics closely related with the channels, such as Bluetooth, NFC, and data transmission speeds.